Building an RBAC Policy
Creating an RBAC Policy is very simple within Permit. Let's run through a simple example that is defined below.
An Administrator within a company can perform all actions on documents
Creating roles (Top Level in the UI)
As part of the RBAC Policy, we need to create specific roles (Top Level in the UI) that will be assigned specific permissions. We are going to create two roles; an admin and a customer.
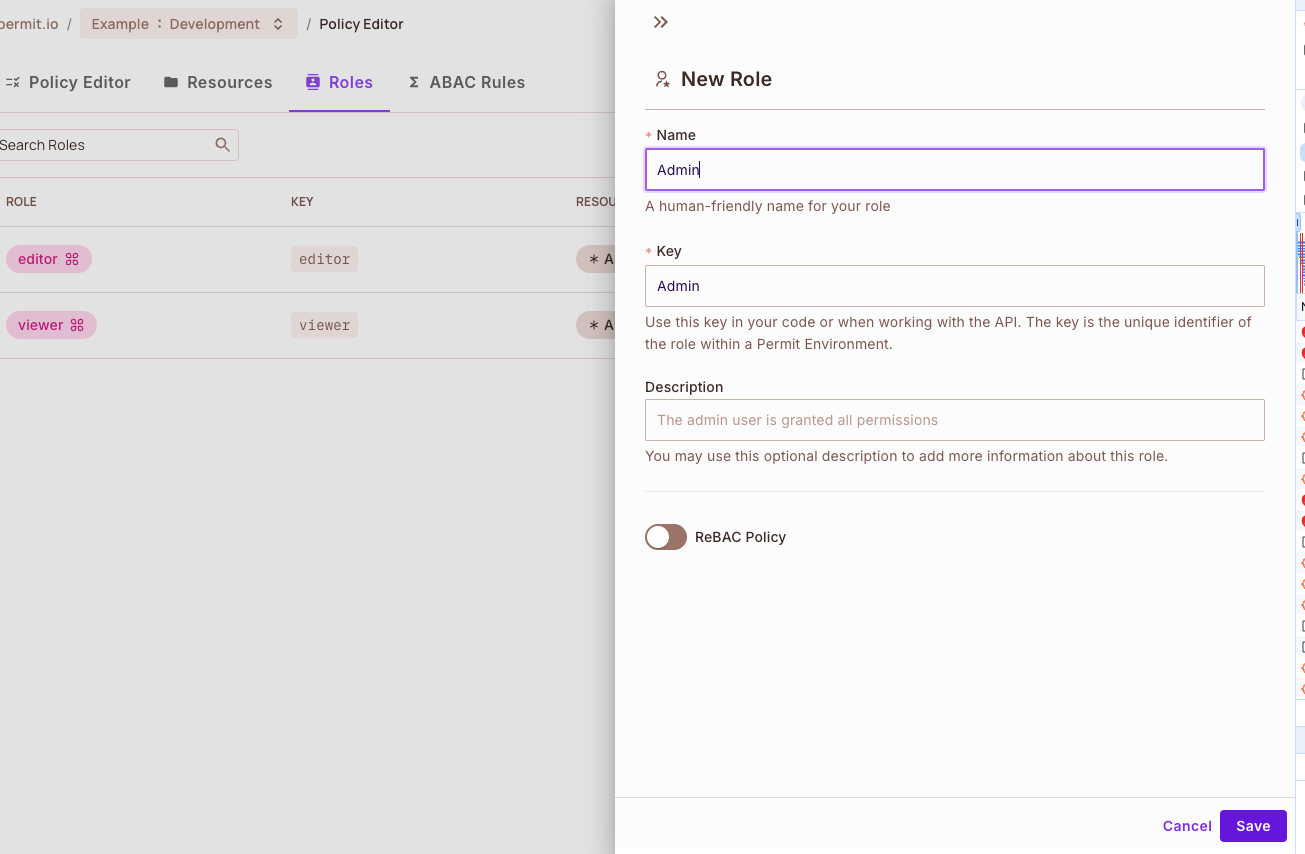
Creating the Admin Role (Top Level) within the UI
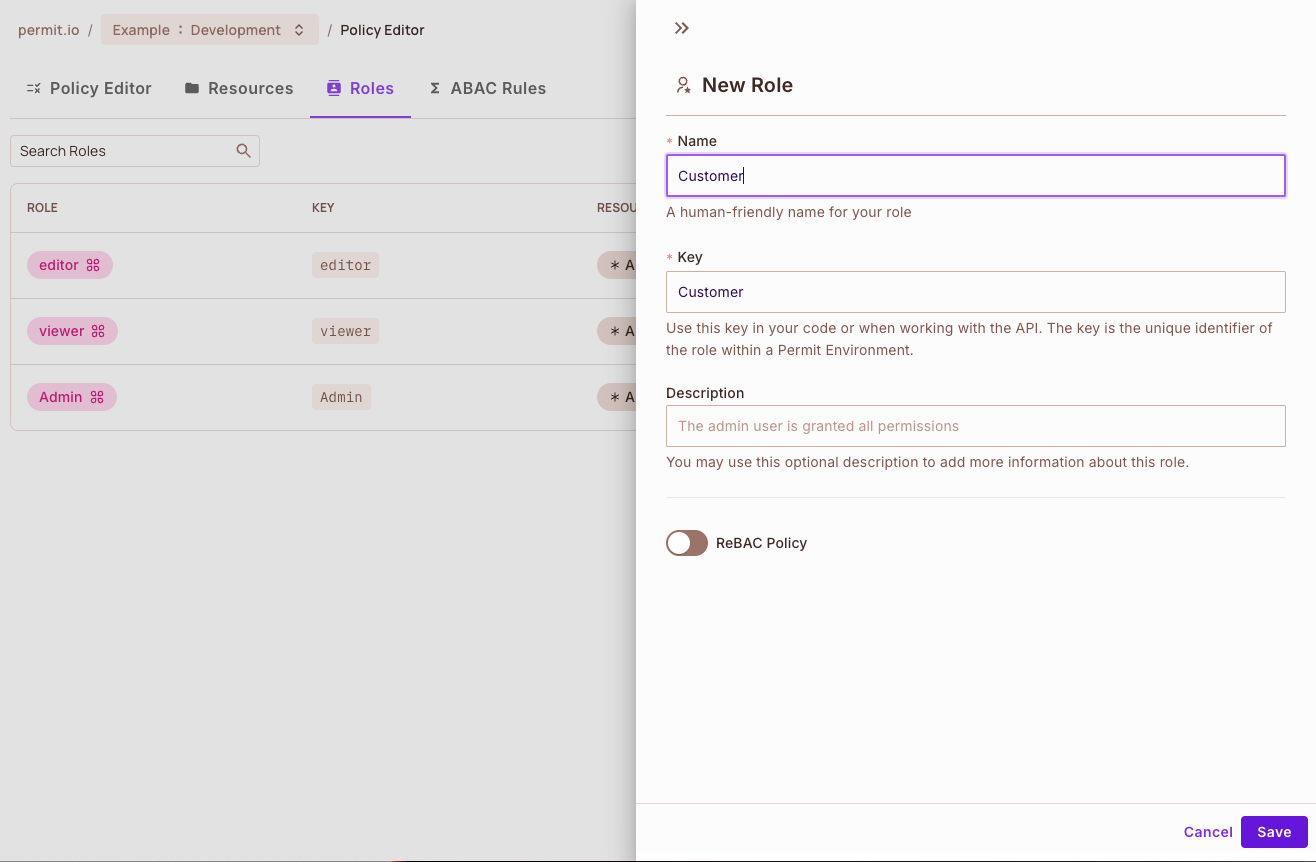
Creating the Customer Role within the UI
Adding a Resource
Once we have established the roles we want within out project, we need to define the resource for the roles. Remember that each created resource becomes available for each role within each project.
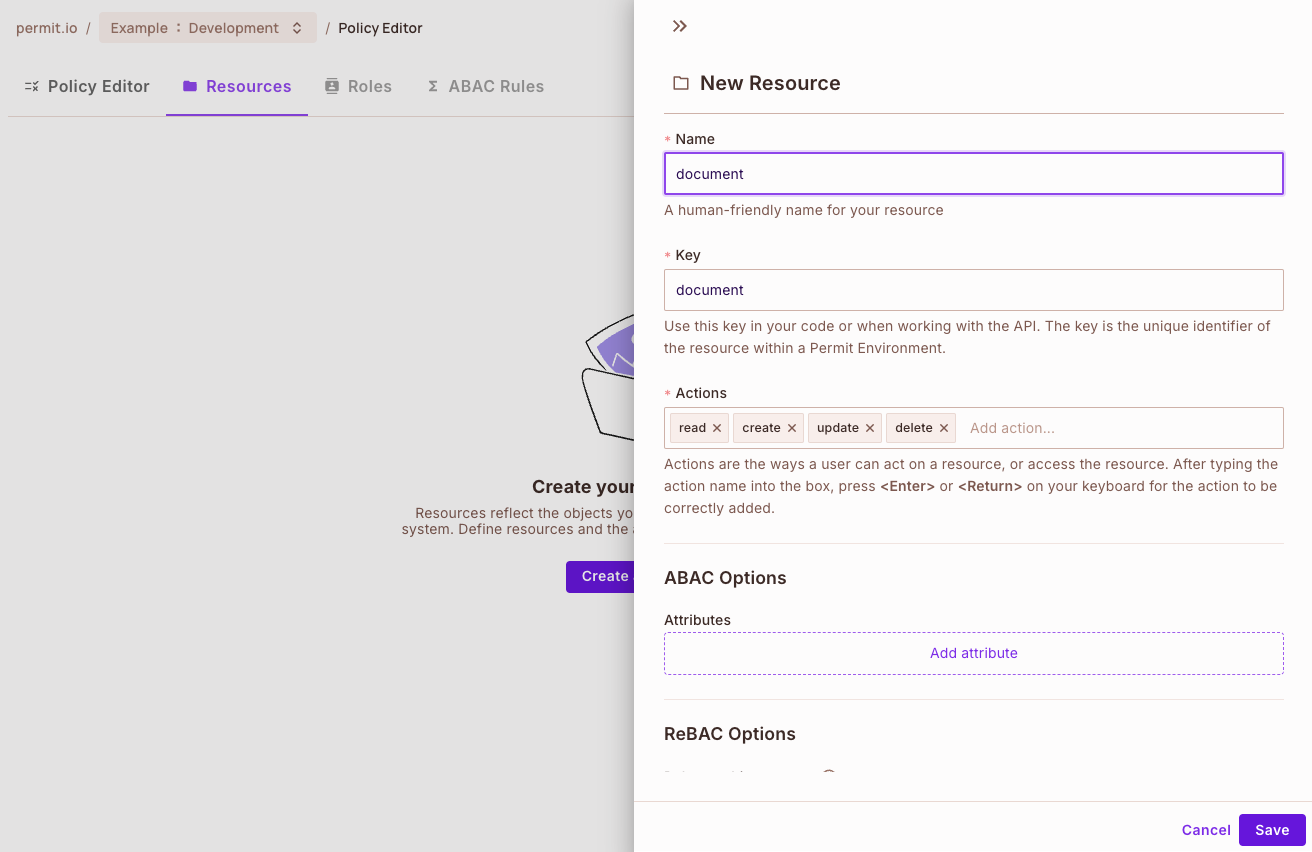
As you can see, we currently have no resources, so lets define a resource called documents. For that specific resource, we need to define the actions that we can perform on the resource. In this case, we can create, read, update and delete documents.
Creating a Resource within the UI
This is what the roles will look like now, with each individual resource defined and the actions that we can select. We are ready give permissions to the role to perform the selected actions on the resource.

Assigning Permissions to Actions
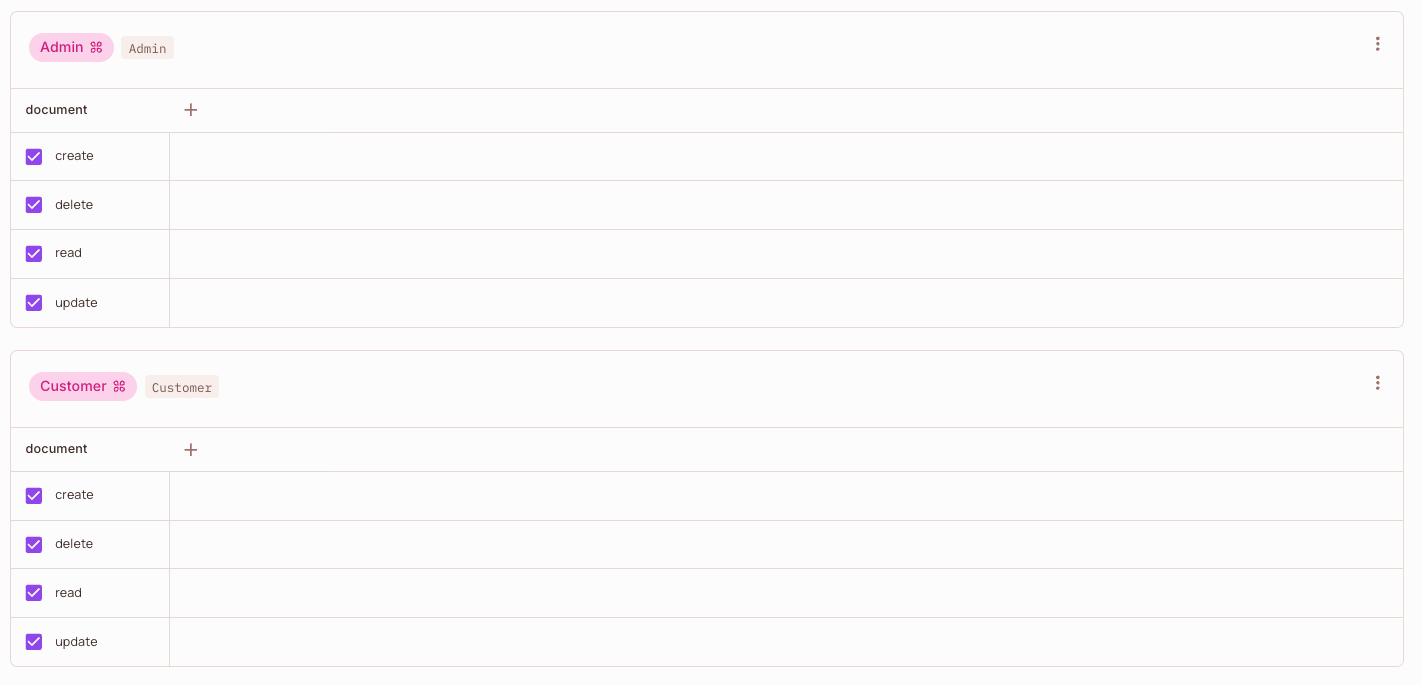
Under each role, we have selected the actions we want to allow that role to perform on the current resource.
Roles with specific selected permissions
Creating a User & Assigning a Role
Now that all our roles as defined with the correct permissions, we need to assign the specific roles to individual users within our company.
The users
We need to navigate to the Users panel to work with users within Permit.
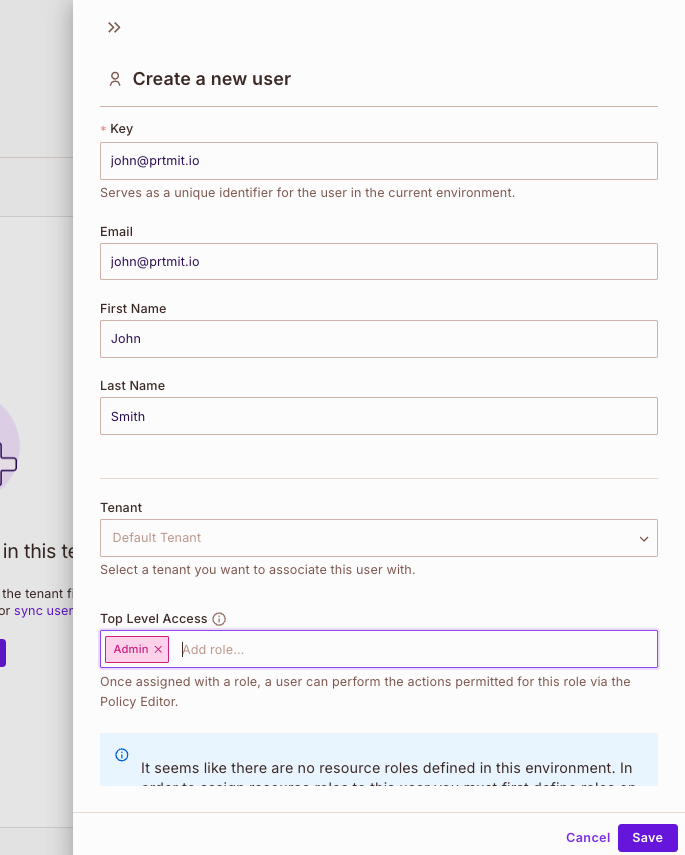
Assigning a role to a user
After the user has been created, we can assign him a role from the roles we have available within out policies.
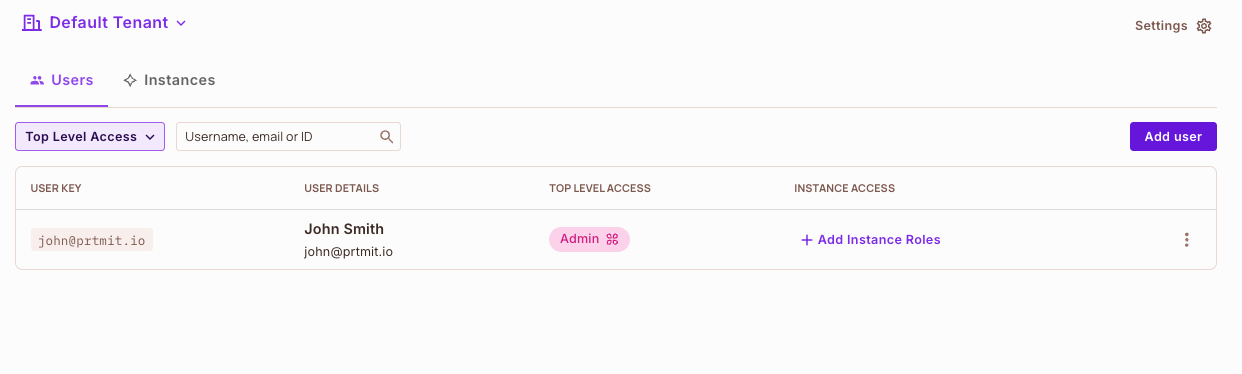
A user with the admin role
Once the user is created and a role is assigned, you can view this users in a rendered table in the Users panel.
Multi-Tenancy RBAC in Permit
While the Top-Level roles in Permit are created at the environment level and shared the permissions/policy, you can control the permissions you assign to users in different tenants using Permit's multi-tenancy model.
For example, when you assign roles to a user, you can assign them an Admin role in one tenant, and Customer role in another.
To learn more about Multi-Tenancy in Permit, refer to this guide
If you'd like to take this tenant isolation and allow your application's tenant admins to own their own roles, you can utilize the API-based role attribute feature in Permit to distinct top-level tenants in the schema. You can read more about role attributes here
Role Attributes
To achieve more granualrity in role creation, we
Congratulations! You have created a simple RBAC Policy!