n8n Integration
Overview
n8n is an open-source workflow automation platform that lets you connect different services and build complex, multi-step automations and AI agents. Integrating Permit with n8n allows you to embed fine-grained authorization checks directly into your workflows, so access control is enforced automatically at any step you choose.
The n8n Permit integration transforms how you handle authorization in n8n workflows by:
- Automating permission checks that can control workflow routing and decision-making
- Enabling real-time authorization validation that redirects workflow execution based on access control results
- Automatically identifying which team members have the authority to approve, review, or process specific requests
- Seamlessly extracting context from incoming data to make intelligent access control decisions
- Creating authorization-driven workflow logic that scales with your organization's permission structure
Quick Start
Prerequisites
Before you begin, ensure you have:
- n8n (cloud or self-hosted)
- A Permit.io account with an API key
- Basic understanding of n8n workflow concepts
- Local PDP container for ABAC/ReBAC policies (optional but recommended)
Installation
Install the @permitio/n8n-nodes-permitio community node via the n8n UI or follow the installation guide.
Configuration
Configure Permit API credentials in n8n with your environment API key and PDP URL:
- API Key: Your Permit.io environment API key from Settings → API Keys
- PDP URL:
- Cloud PDP:
https://cloudpdp.api.permit.io(default) - Self-hosted PDP: Your PDP's network-accessible URL:
- Same machine:
http://localhost:7766 - Different server:
http://your-pdp-server:7766 - Docker network:
http://pdp-container:7766 - Kubernetes:
http://pdp-service.namespace:7766
- Same machine:
- Cloud PDP:
For ABAC and ReBAC policies, use a local PDP container for better performance and advanced policy support.
Core Operations
The Permit node provides three core operations:
- Check Permissions: Verify if a user can perform an action on a resource
- Get User Permissions: Retrieve all permissions for a specific user
- Get Authorized Users: Find users who can perform actions on resources
Each operation integrates with n8n's expression system for dynamic authorization workflows.
Authorization Models
The n8n Permit integration supports all three authorization models, allowing you to choose the right approach for your use case.
Role-Based Access Control (RBAC)
Grant permissions based on user roles. Simple and effective for basic authorization needs.
{
"user": "alice@company.com",
"action": "read",
"resource": "document"
}
Attribute-Based Access Control (ABAC)
Make authorization decisions based on user, resource, and environmental attributes. The node automatically extracts attributes from webhook payloads when Enable ABAC is checked.
{
"user": "john.employee",
"action": "submit",
"resource": "expense",
"attributes": {
"expense_amount": 1500,
"category": "Travel",
"department": "Engineering"
}
}
Relationship-Based Access Control (ReBAC)
Control access based on relationships between users and specific resource instances.
{
"user": "manager@company.com",
"action": "approve",
"resource": "expense",
"resource_key": "exp-123"
}
Use a local PDP container (http://localhost:7766) for ABAC and ReBAC policies. Cloud PDP supports RBAC workflows.
Practical Example: Expense Approval Workflow
This example demonstrates building an automated expense approval system using ABAC policies with the Permit n8n node.
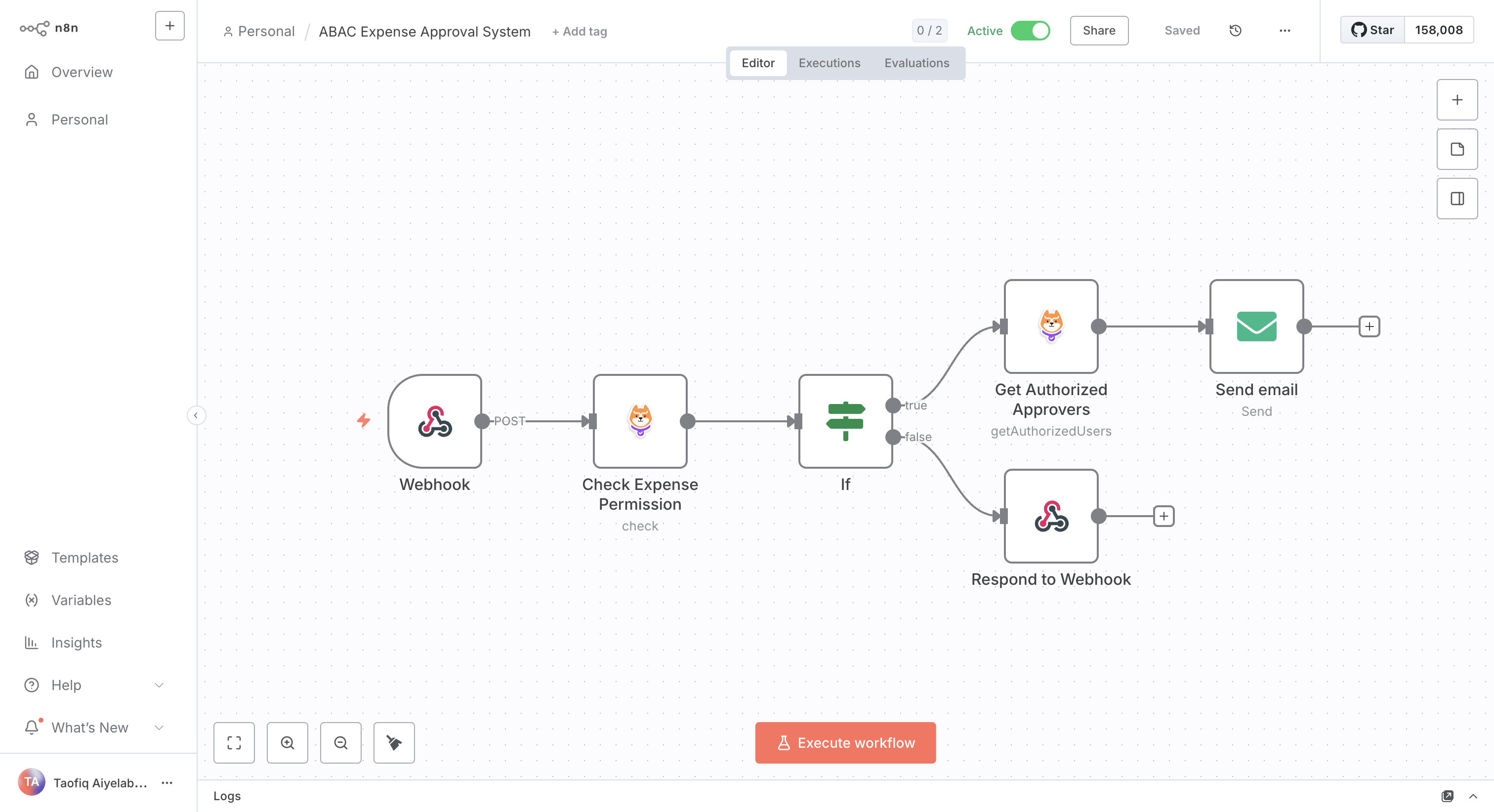
Workflow Architecture
Node Configuration
1. Webhook Node Receives expense submissions with employee data and expense details.
2. Permit Check Node
- Operation: Check
- User:
{{$node['Webhook'].json.body.employee_email}} - Action:
submit - Resource:
expense - Enable ABAC: (automatically extracts
expense_amount,category, etc.)
3. IF Node Routes based on permission result: approved requests go to user lookup, denied requests return error.
4. Get Authorized Users Node
- Operation: Get Authorized Users
- Action:
approve - Resource Type:
expense - Resource Attributes:
{"expense_amount": 1500, "category": "Travel"}
5. Send Email Node Notifies authorized approvers about pending expense requests.
Example Payloads
Approved Request:
{
"employee_email": "john.employee",
"expense_amount": 1500,
"category": "Travel",
"description": "Client meeting"
}
Response: Email sent to authorized approvers.
Denied Request:
{
"employee_email": "john.employee",
"expense_amount": 2500,
"category": "Travel"
}
Response: {"error": "Access denied", "reason": "Exceeds spending limit"}
Operations Reference
Check Permissions
Verify if a user has permission to perform a specific action on a resource.
Configuration:
- User: User identifier (supports expressions)
- Action: Action to check (e.g.,
read,write,submit) - Resource: Resource type (e.g.,
document,expense) - Tenant: Tenant identifier (defaults to
default) - Enable ABAC: Auto-extract attributes from webhook payload
- Resource Key: Specific resource instance (for ReBAC)
Response:
{
"allow": true,
"decision": "2024-01-15T10:30:00Z",
"debug": {
"reason": "User has required permissions"
}
}
Get User Permissions
Retrieve all permissions for a specific user across resources.
Configuration:
- User: User identifier
- Resource Types: Comma-separated list (e.g.,
expense,document) - Enable ABAC: Include attribute-based permissions
Response:
{
"permissions": [
{
"resource": "expense",
"action": "submit",
"allowed": true
},
{
"resource": "document",
"action": "read",
"allowed": false
}
]
}
Get Authorized Users
Find all users who can perform a specific action on a resource.
Configuration:
- Action: Action to check (e.g.,
approve) - Resource Type: Resource type (e.g.,
expense) - Tenant: Tenant identifier
- Resource Attributes: JSON object with resource attributes
- Enable ABAC: Include attribute-based user discovery
Response:
[
{
"resource": "expense:*",
"tenant": "default",
"users": {
"finance.admin@company.com": [
{
"user": "finance.admin@company.com",
"role": "finance_approver"
}
]
}
}
]
Getting Help
Next Steps
Now that you have the basics, explore:
- Attribute-Based Access Control (ABAC)
- Relationship-Based Access Control (ReBAC)
- Policy as Code with Terraform
- Self-Deployed PDP Setup
- Permit CLI for Automation
Need Help? Join our Slack community or check out our GitHub repository for support and examples.