Simple URL Mapping Check
The Simple URL Mapping Permissions Check is a powerful feature that allows you to control access to your application's endpoints based on URLs.
FoAz is deprecated and no longer supported, but it is still available at app.permit.io/foaz-proxy .
For URL-Based permission - we’re introducing app.permit.io/url-mapping.
Overview
URL Mapping in Permit.io enables you to:
- Map HTTP URLs to specific resources and actions within your application
- Control access based on URL patterns and HTTP methods
- Extract parameters from URLs for use in permission rules
- Implement flexible and maintainable URL-based access control
This feature is available through the FoAz UI & PDP. You can access the FoAz UI inside the Permit App here.
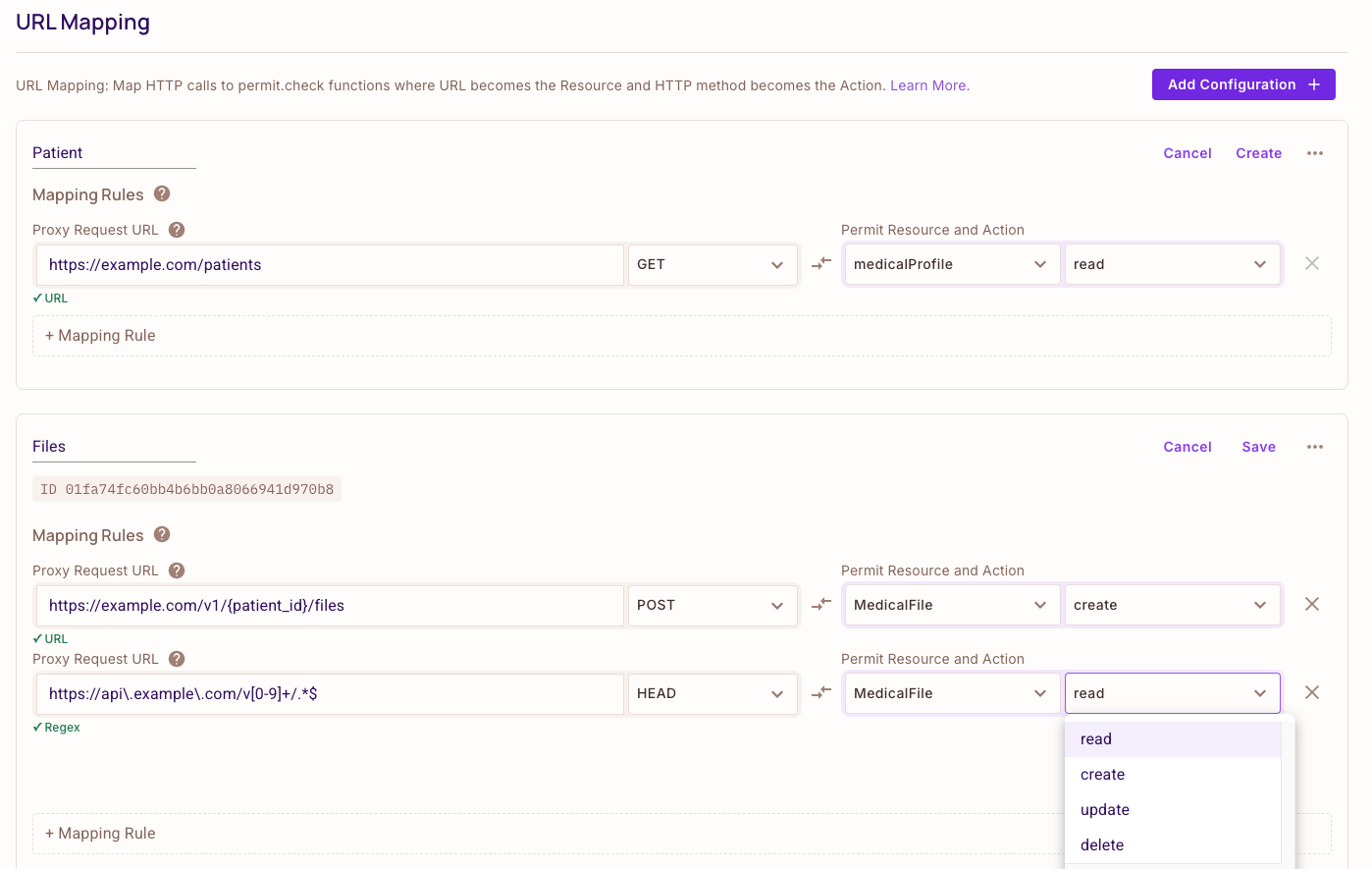
Simple URL Mapping
Simple URL Mapping uses a straightforward {var} syntax to define path parameters in your URLs. This approach is ideal for basic URL patterns where you need to extract simple path parameters.
Basic Concepts
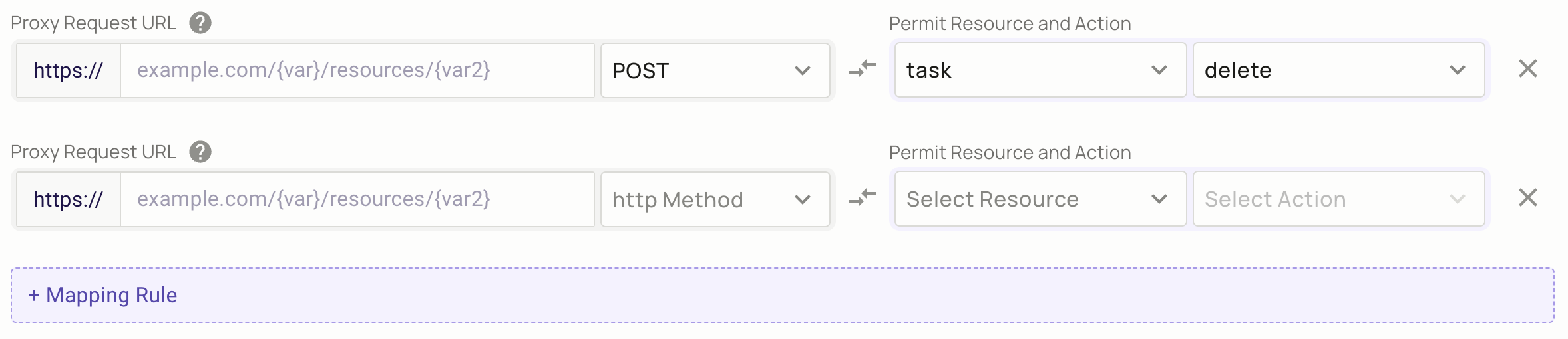
In FoAz UI, you can set variables as part of the URL using the following syntax: {var1}. This feature is called templating the URL, and it's beneficial to reduce the overall number of mapping rules required.
For example, you might set up a URL like this: example.com/v1/{customer_id}/payments.
In this case, {customer_id} is a placeholder that will be replaced with the actual customer ID during the request. This strategy allows you to use a single mapping rule for all customers, rather than needing a separate rule for each customer.
Setting Up Simple URL Mapping
The mapping rules feature in the FoAz UI links HTTP URLs to particular resources and actions within the Permit.io platform. These rules are essential for controlling access and permissions on your website or application.
By correctly setting up mapping rules, you can ensure that requests are correctly routed and that users only have access to the resources that they are authorized to view or modify.
Checking Permissions
To use the URL Mapping Permissions Check, you must first start your PDP.
docker run -it \
-p 7766:7000 \
--env PDP_API_KEY=permit_key_{your_permit_env_key} \
--env PDP_DEBUG=True \
permitio/pdp-v2:latest
Simple URL mapping is supported in PDP version 0.2.19 or higher
Currently, checking permissions using URL Mapping is available through the endpoint /allowed_url on the PDP. The SDKs will be updated to support this feature soon.
Here's an example of a payload to localhost:7766/allowed_url (assuming you're running the PDP locally):
curl --location 'http://localhost:7766/allowed_url' \
--header 'Content-Type: application/json' \
--header 'Accept: application/json' \
--header 'Authorization: Bearer permit_key_{your_key}' \
--data '{
"user": {
"key": "raz@permit.io"
},
"url": "https://example.com/endpoint?param=value",
"http_method": "POST",
"tenant": "default"
}'
You can see more details about the payload in the PDP API Redoc